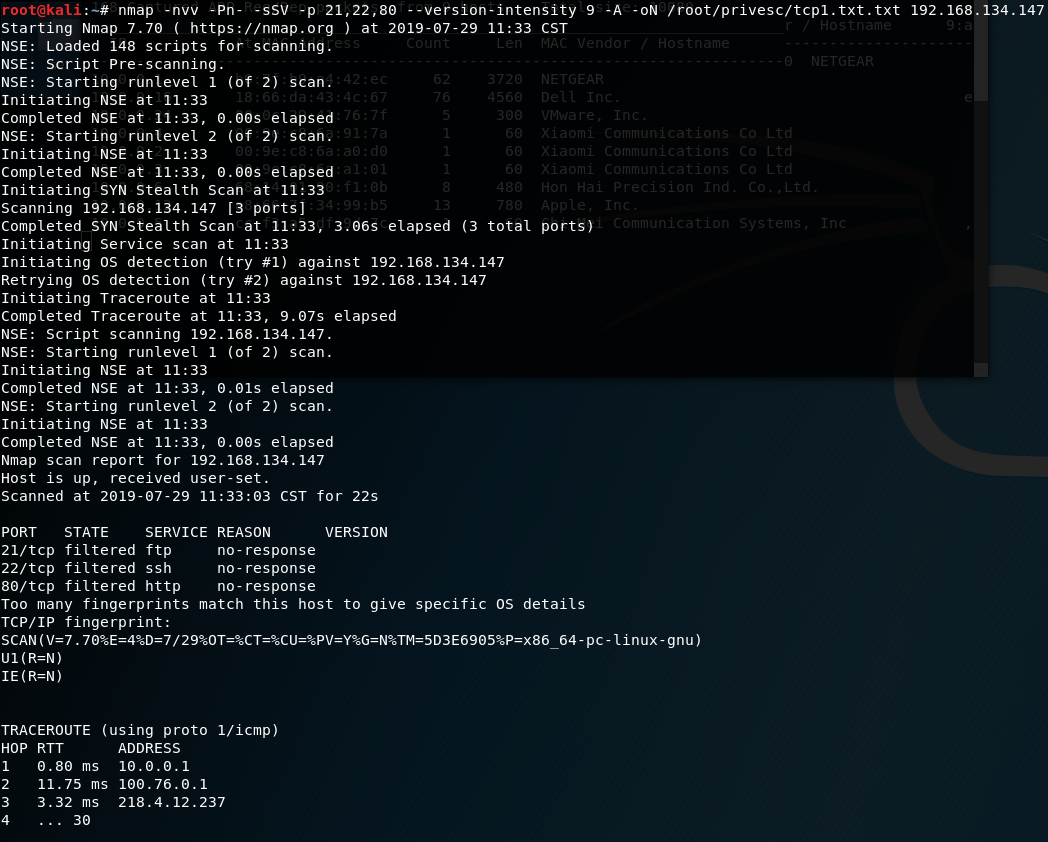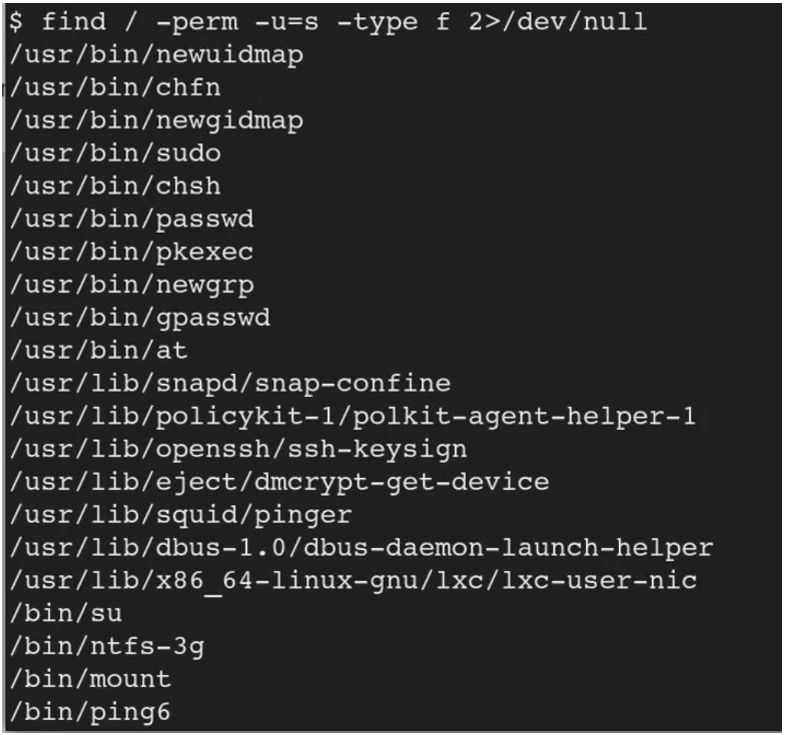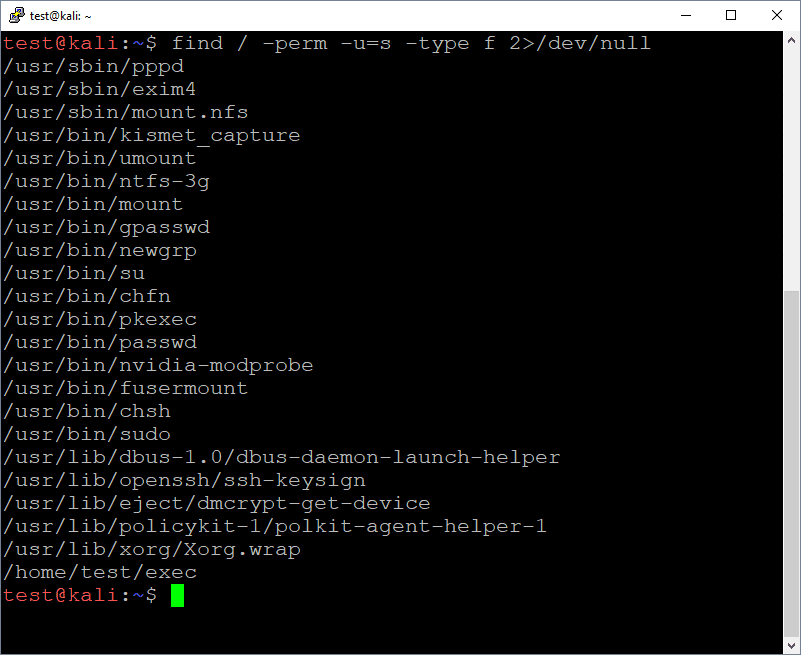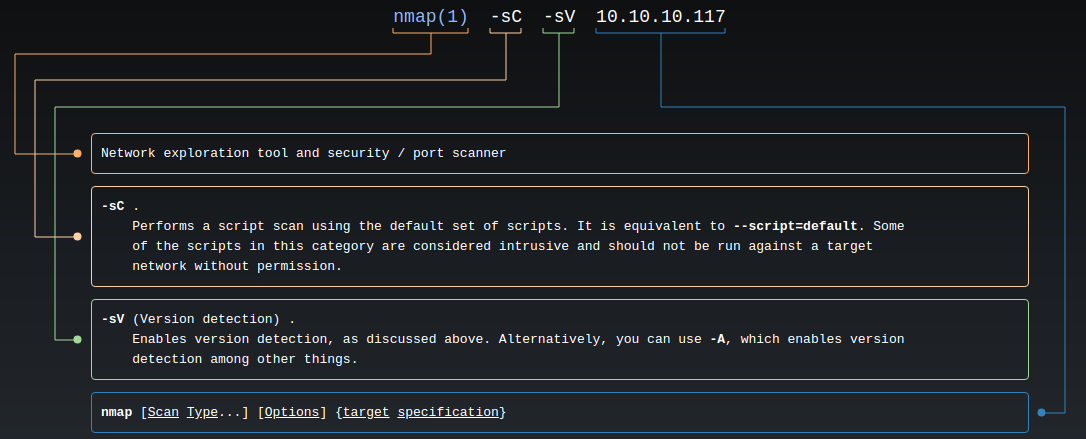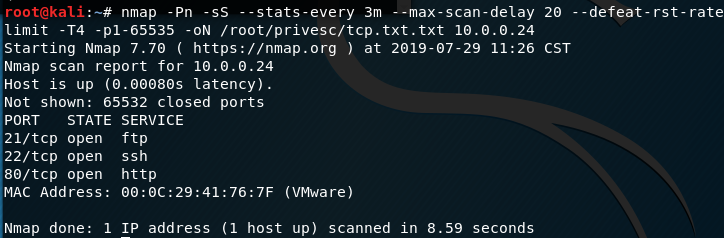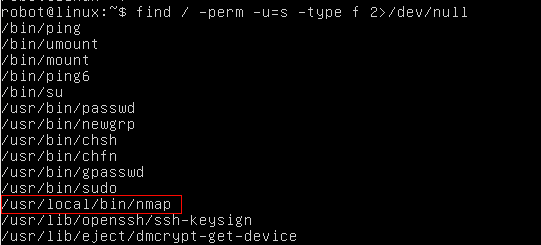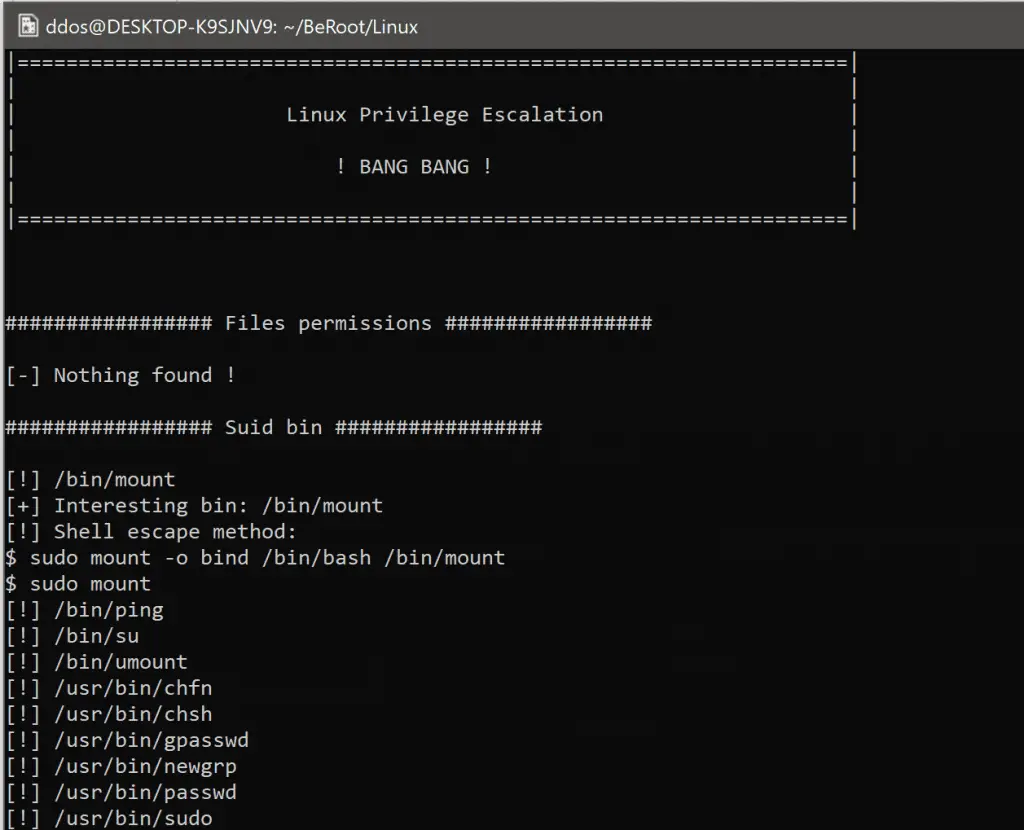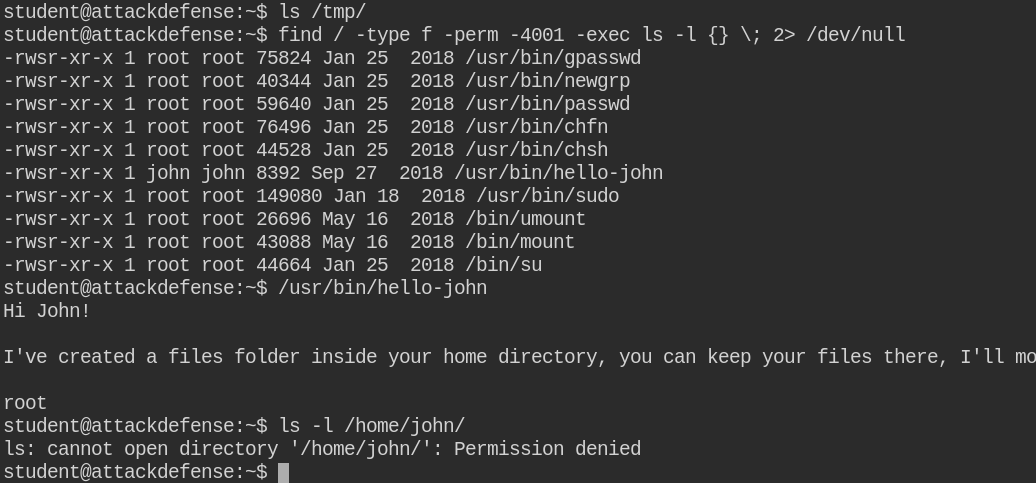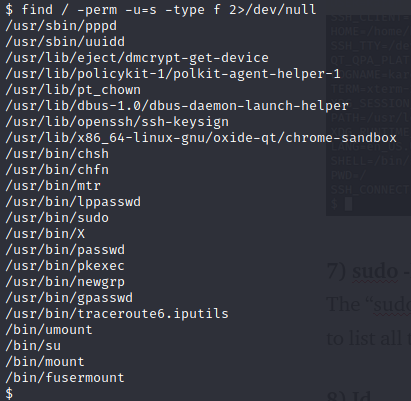
Series of CTF machines Walkthrough #4 Linux Privilege Escalation (Enumeration). | by C M UPPIN | Techiepedia | Medium

Linux Privilege Escalation Abusing Shell Features – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis



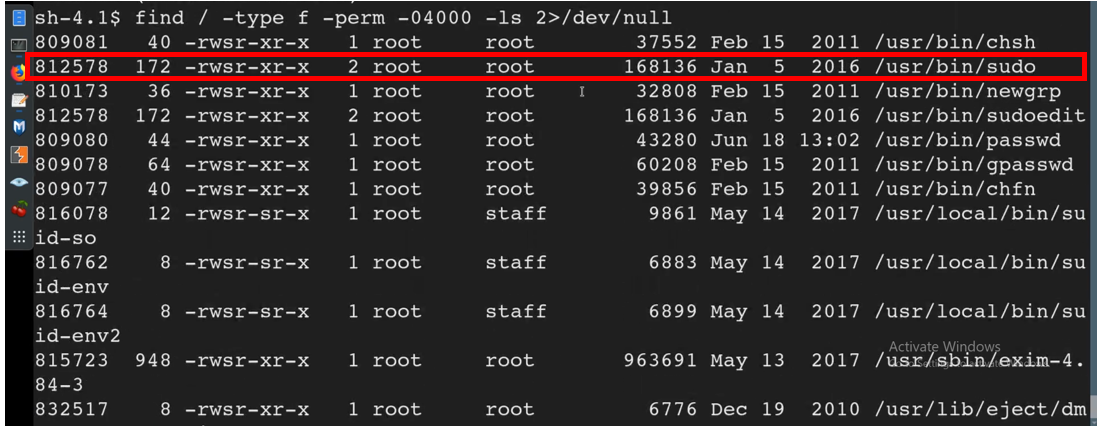



![Linux PrivEsc [TryHackMe] – Revx0r – Security Mindset Blog Linux PrivEsc [TryHackMe] – Revx0r – Security Mindset Blog](https://i0.wp.com/revx0r.com/wp-content/uploads/2021/11/linprivesc.jpg?fit=549%2C212&ssl=1)